Apache CloudStack is one of the most commonly used IaaS platforms, orchestrating infrastructure and maximizing the benefits of cloud computing. Many large enterprises already use CloudStack with different use cases, and with ever-growing adoption, there is a need to automate these complex infrastructures and the provision of cloud deployments to:
· Minimise time spent on deploying new environments
· Make cloud deployments repeatable
· Reduce cost
· Avoid human error
A popular infrastructure provisioning tool used to manage cloud configuration and deployment is Terraform. By using Apache CloudStack with Terraform, companies can easily automate their infrastructure to take advantage of the aforementioned benefits.
About Terraform

Terraform is an open-source infrastructure code software tool that provides consistent workflows to manage hundreds of cloud services, codifying cloud APIs into declarative configuration files.
Terraform allows infrastructure to be expressed as code in a simple, human-readable language called HCL (HashiCorp Configuration Language). It reads configuration files and provides an execution plan of changes, which can be reviewed for safety and then applied and provisioned. Extensible providers allow Terraform to manage a broad range of resources, including IaaS, PaaS, SaaS, and hardware services
Terraform Integration with Apache CloudStack
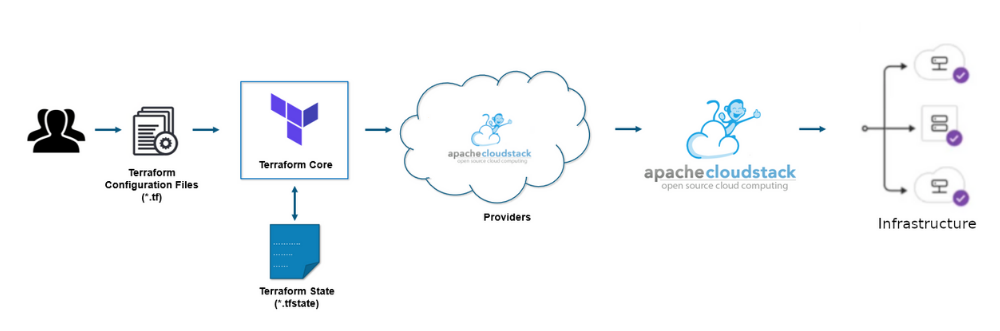
Terraform relies on plugins called Providers to provision or manage resources in the cloud. As part of the integration between Terraform and Apache CloudStack, Terraform requires a CloudStack specific provider which acts as a transition layer between Terraform and CloudStack. This provider is written to provision and manage resources like virtual machines, networks, templates, volumes, etc., using the CloudStack API. The latest release of the Apache CloudStack Terraform Provider is 0.4.0, and is the first release after the provider was brought under the Apache 2 license. Terraform Core is the engine that transfers the user’s requirements into action. For that, it requires a configuration file (*.tf) as an input in which users define what cloud resources need to be provisioned and managed. The HCL is used to prepare the configuration file. Terraform also uses another input source. The state file (*.tfstate) holds the state information of the resources created or managed by Terraform and is used to create action plans whenever the configuration is applied. Once the actions are performed, Terraform syncs with CloudStack and keeps this state file up to date.
Once the action plan is created and confirmed by the user, Terraform uses the CloudStack Provider to apply those actions in CloudStack. When complete, Terraform fetches the resource states and saves them to its state file.
With the predefined or newly-generated configuration files, admins can use the same versioning principles which developers use when writing code. This provides many benefits, such as:
· Reliability – a preview of changes, mistakes can be rolled back
· Transparency – who did what
· Automation and repeatability – the pre-defined configuration can be generated on different environments, for example, development and QA, making sure they are exactly the same
· Idempotence – ‘apply’ command always sets the target environment into the same configuration, regardless of the environment’s starting state
· Keeping a history of infrastructure changes
An Example Setup Using Terraform and Apache CloudStack
Let’s go through an example using Terraform and an Apache CloudStack / KVM environment to create a few resources. We will see multiple .tf files having relevant configurations in each file.
Create a Terraform folder (say /TerraformProvider) and create a file main.tf in that folder.
The file main.tf contains the following configuration with the details of terraform provider and CloudStack environment, ensuring you enter the proper API and Secret Key for the CloudStack admin user:
terraform {
required_providers {
cloudstack = {
source = "cloudstack/cloudstack"
version = "0.4.0"
}
}
}
provider "cloudstack" {
# Configuration options
api_url = var.api_url
api_key = var.api_key
secret_key = var.secret_key
}
variable "api_url" {
description = "API URL"
type = string
default = "http://x.x.x.x:8080/client/api"
}
variable "api_key" {
description = "API key"
type = string
default = "XXXXXXX"
}
variable "secret_key" {
description = "Secret key"
type = string
default = "YYYYYYY"
}
Now initialise the Terraform provider which will download the version specified in the Terraform configuration file, in this case, “0.4.0”:
$ terraform init
Create file cloudstack_network.tf:
resource "cloudstack_network" "isolated_net" {
name = "TERRAFORM-isolated"
cidr = "10.0.0.0/24"
network_offering = "DefaultIsolatedNetworkOfferingWithSourceNatService"
zone = "zone1"
}
Create file cloudstack_template.tf:
resource "cloudstack_template" "template1" {
name = "Macchinina"
os_type = "Other Linux (64-bit)"
zone = "zone1"
url = "http://dl.openvm.eu/cloudstack/macchinina/x86_64/macchinina-kvm.qcow2.bz2"
format = "QCOW2"
hypervisor = "KVM"
}
And finally the cloudstack_instance.tf file:
resource "cloudstack_instance" "VM1" {
name = "TERRAFORMVM1"
service_offering = "Small Instance"
template = cloudstack_template.template1.id
network_id = cloudstack_network.isolated_net.id
zone = "zone1"
expunge = true
}
Now we can issue the Тerraform apply command:
$ terraform apply ….. Apply complete! Resources: 3 added, 0 changed, 0 destroyed.
We can verify that the template, network, and VM indeed are present in CloudStack.
Now let’s try changing the VM name from TERRAFORMVM1 to TERRAFORMVM2 in file cloudstack_instance.tf and apply the modified configuration:
$ terraform apply …. Apply complete! Resources: 0 added, 1 changed, 0 destroyed.
And finally let’s try destroying the created resources:
$ terraform destroy …. Destroy complete! Resources: 3 destroyed.
By using Apache CloudStack and Terraform, users can automate infrastructure deployment and essential resources such as virtual machines, isolated networks, VPC, VPN, and security groups (comprehensive list at https://registry.terraform.io/providers/cloudstack/cloudstack/latest/docs). The integration between CloudStack and Terraform will be enhanced in future releases by adding more and more resources to the CloudStack provider, making it easier to manage infrastructure across clouds, quickly reproduce existing setups in hybrid environments, and simplifying overall infrastructure management.
Test Drive Apache CloudStack
Experience first-hand how Apache CloudStack can streamline cloud operations and support the creation of customizable, multi-tenant infrastructure as a service (IaaS) environments.
Harikrishna works at ShapeBlue as a Software Engineer, and is also engaged with active development of new features and capabilities for the Apache CloudStack project. He has been working on CloudStack since 2012 and is a committer in this project. Before joining ShapeBlue, Harikrishna worked for Citrix Systems and Accelerite. He holds an M.Tech in Computer Science and Engineering from IIT-Madras.
You can learn more about Harikrishna and his background by reading his Meet The Team blog.






